Cyber Threat Intelligence is an important component of any effective security program. The elevated increase of high-profile breaches in recent years has led to an increasingly complex and stringent compliance regime. Depending on your business vertical, you may already have some familiarity with the Payment Card Industry – Data Security Standard (PCI-DSS), Health Insurance Portability and Accountability Act (HIPAA), National Institute for Standards and Technology (NIST) Cyber Security Framework, and 800-53. The ultimate objectives of all of these standards in to ensure the protection of personal data held by our companies. Although building your security program around a particular compliance regime may insure compliance with that regime, it may not provide the best security posture for your organization.
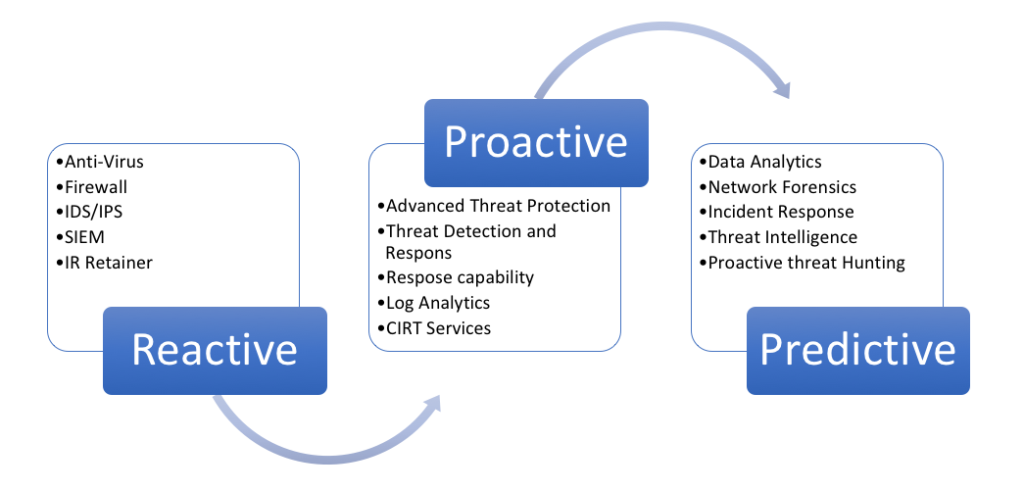
To be clear, I am not suggesting that compliance is unimportant or to be ignored. However, I am a proponent of intelligence-led security programs, as intelligence - not compliance - should drive your security program. Our overall objective should be to move from a reactive security posture to one that is predictive.
The first thing to understand is your organizational risk and threat profile. You must position your resources against the threats that matter to YOUR organization. In order to effectively do this, you must first understand what your threat landscape looks like and establish the organizational risk tolerance within your organization.

A good friend once said (he says it all the time actually) “the first rule in cyber security is to know thyself.” To that end, you might consider your answers to the following questions:
- What sector am I in? Am I considered "critical infrastructure"?
- What are my business units, how are they interconnected?
- What is my geographic footprint (the EU has a very different view of PII than we have in the US)?
- Who are my partners?
- Who are my customers?
- What/where are my assets?
- What is our threat history?
- What data do I hold/process (customer data, HR data, business critical data, etc.)?
Once you have a firm understanding of your organizational risk, the next step is to understand your stakeholders and consumers. What are the roles of the consumers of your intelligence; what information is relevant for them? In what format and in what degree of frequency would they like to receive intelligence? What are the use cases for your consumers? Understanding the various use cases should allow you to tailor the intelligence for your customers, thereby increasing the value to your organization.
You must also establish your intelligence requirements?
Some questions to help establish requirements might include, but are not limited to, the following:
- What intelligence is needed by our customer?
- What vulnerabilities are being exploited in the wild?
- Can we detect and defend against those exploits?
You must also establish collection requirements.
- Liaison with like organizations within your business sector
- Liaison with other members of the information security community
- Open source feeds
- Online forum monitoring where exploitation and vulnerabilities are discussed
- Blog monitoring
Establishing requirements should allow for effective response to incidents. The intelligence must be categorized and prioritized in a way that allows for detection and response to the most critical information with the requisite speed and resources.
You must also develop sources (subscribed intelligence feeds, indigenous intelligence and/or intelligence provided by one of the many government entities) to maximize the intelligence value. Finally establish the expected actions on the intelligence.
Implementing Practices for Intelligence-Driven Security Programs
Step two is developing best practices (methods) for managing the intelligence life cycle. That lifecycle should include building and analytic framework, developing your analyst tradecraft and expertise, collection and processing, develop relevant production standards, etc. Subsequently, or simultaneously, you must integrate intelligence within your technology stack. This could include feeds into your SIEM, Content Management System, anti-virus, endpoint technology, network traffic analysis tools, etc.
Realizing Capabilities
Assuming a strong foundation and the development of best practices, the benefit is realizing the capabilities. A mature intelligence program should provide a myriad of benefits to the enterprise, including:
- Provide for proactive threat detection
- Effective and repeatable threat communications
- Effective two-way information sharing
- Threat trending and predictive analytics
- Proactive threat detection
- Analytic/tactical support to security operations
- Enterprise strategic decision support
I started this conversation with a statement that I believe in intelligence over compliance-driven security programs. Compliance does matter, but the fact is that you can do both at the same time. However, the intelligence-driven security model allows for the best opportunity to achieve a predictive security state.