Observability is a way of monitoring and tracking security related events and activities within an organization’s network. Using Crowdstrike’s words, “observability is when you infer the internal state of a system only by observing its external outputs.” Observability is increasingly important as networks and hybrid infrastructures become more and more complex. Data stores are becoming larger and larger as time progresses. Being able to effectively monitor and understand your data is integral to the efficacy of data-driven operations. If observability is implemented well then an outside observer would be able to infer the health of the system only using the outputs.
Data stores are continually expanding as time progresses. Effectively monitoring and understanding your data is integral to the success of data-driven operations. Consortium Networks along with NetBuilder and Cribl can help to overcome the issue of observability. One of the solutions we offer is integrating and optimizing Cribl activations to best fit your company. Many companies in today’s market are advised to purchase various software packages when what they already own is sufficient if used correctly. Consortium Networks can ensure you are utilizing your newly activated Cribl software to its fullest potential. We help companies seamlessly integrate Cribl to optimize data routing and enrichment, ensuring maximum efficiency and control over your data pipelines.
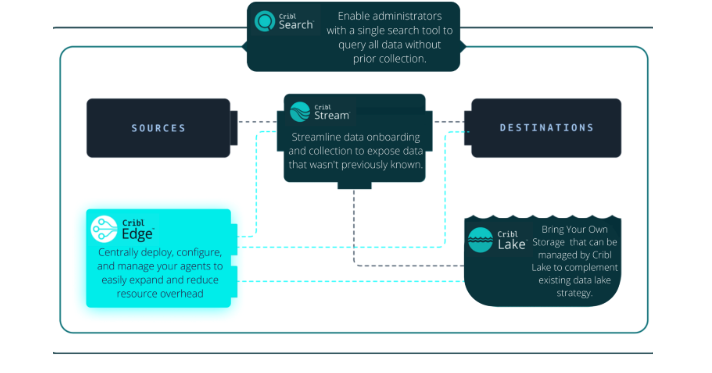
At Consortium Networks we specialize in addressing challenges related to managing advanced data processing flows for your company. We can help find scalable solutions for comprehensive data management including the integration of Cribl Stream, Edge, Lake, and Search for optimized data flow. We also use our unique L and N model that includes the combination of Leadership (L) and Engineers (N) to ensure a high quality deployment and cost effective efficiency. We can help to incorporate the Data Lake solutions from Cribl Lake to maximize observability to best give your organization a cutting edge. This solution allows for easy data storage, management, and access which leaves more time for your cybersecurity team members to focus on more pressing issues. Our approach ensures that your organization benefits from enhanced visibility and proactive threat management, leveraging advanced technologies to streamline operations and strengthen cybersecurity posture.